Apple have been the highlight of a high profile bug in their iOS and OS X platforms recently with the SSL bug recently reported. Apple rolled out the patch to address that exploit, but a new report shows yet another vulnerability in iOS which this time allows attackers to access, record, and monitor every single touch you make on your device, including keystrokes on the keyboard.
The new vulnerability in iOS was discovered by FireEye and is present on non-Jailbroken iPhones and iPads running iOS version 7.0.4, 7.0.5, and 7.0.6, as well as those running on 6.1.x.
FireEye demonstrates that they’ve created a proof of concept monitoring App in collaboration with Apple that records touch events for a user in the background without their consent or knowledge.
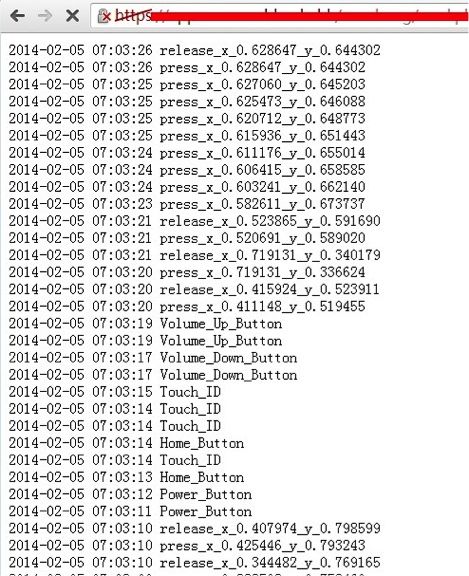
We have created a proof-of-concept “monitoring” app on non-jailbroken iOS 7.0.x devices. This “monitoring” app can record all the user touch/press events in the background, including, touches on the screen, home button press, volume button press and TouchID press, and then this app can send all user events to any remote server, as shown in Fig.1. Potential attackers can use such information to reconstruct every character the victim inputs.
What can the iOS exploit record?
The new iOS vulnerability uses resources usually reserved for apps to run in the background to register presses on the screen, home button, volume button, and TouchID, recording the input and logging it all unknown by the user.
The monitoring app only logs the X and Y coordinates of the touch inputs on the screen, but that could quite easily be referenced out to identify the exact keys pressed.
Whilst this app is in collaboration with Apple, the vulnerability could quite possibly and easily be utilised by an attacker, and use a phishing method to install a malicious app that could exploit it and begin recording activity.
A fix for the bug is apparently in the works and is pending approval to fix the vulnerability, but a fix in the meantime is for users to close apps running in the background to avoid any potential exploits that could be running.