In this article, we’re going to be talking about firewalls. What they are, what they do, and also the difference between traditional and next-gen firewalls. So First, what is a firewall? If you drive or you’re into cars then you may be familiar with the term. If your engine explodes and catches fire there is something called a firewall that separates and shields you from the burning hot flames and network firewalls work in the same way.
Introduction
Contents
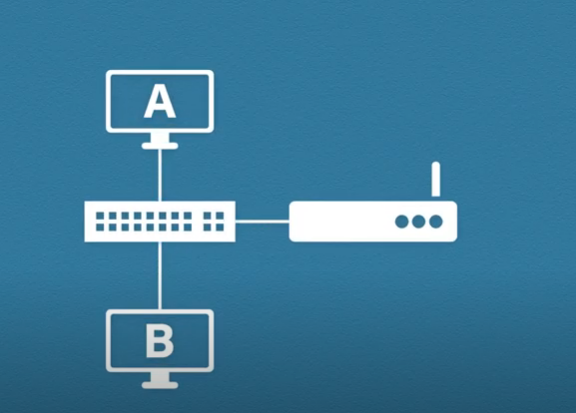
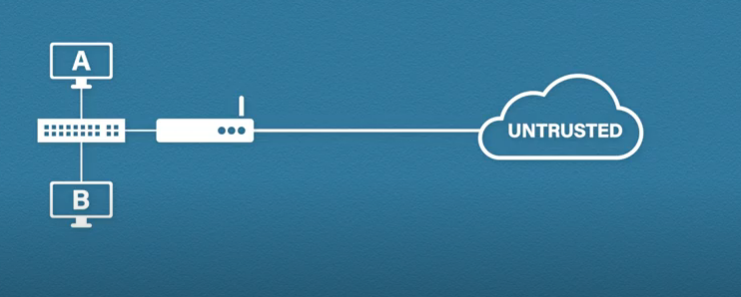
Let’s take this basic network as an example. We have two hosts: a switch and a router. Because you as a company or as an admin have control over these devices, policies, antivirus, etc, it’s reasonable to consider this as a trusted network, but we have zero control over the devices and networks outside our own. So it’s fair to consider these as untrusted networks.
As you know the world is full of a lot of people but some are good and some are bad. Bad guys always try to do bad, This means they try to destroy computer systems. The firewall comes in handy to stop the bad guys and protect networks from untrusted persons.
On a specific network, the firewall will try to block all the bad traffic to secure this network from malicious guys.
How Firewall Block Traffic
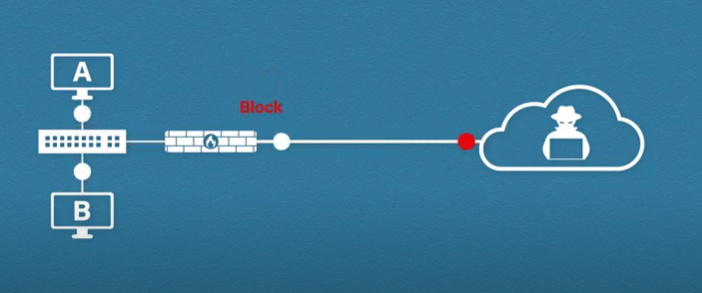
Most of the firewalls by default block everything. This means it will block all the traffic that comes from an unauthorized source to a network. If you want to allow some traffic to your network then you can do this by adding firewall rules.
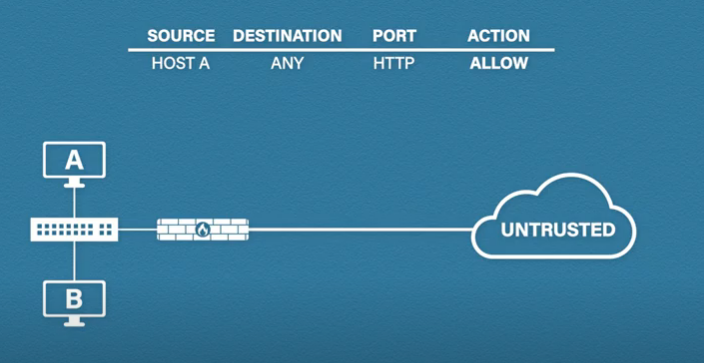
We have to add something called to rule and here the source is the host A the destination is any because we’re not going to add a list of every possible web server, and the port is HTTP or HTTPS, and we’ll set the action to allow. The exact firewall rule format will vary from vendor to vendor. Now, when host A sends traffic the firewall will see this and think are you from host A? Yes. Are you going to ‘any’ IP address? Yes, are you using HTTP? Yes. Okay, you are allowed. And it lets the traffic through
If host B tries to send traffic the firewall checks its rules, sees that there are no matching rules, and blocks the traffic. So now let’s add a rule for host B. Source, host B, destination ‘any’ Port, this time we’ll choose ‘any’ port, not a recommended rule but it will do for the sake of the example. Both host A and host B can send traffic through the firewall So that’s traffic leaving the network, but what about traffic entering the network?
Well, it’s a good idea to block all traffic from external sources. The only exception is in special cases where you need to open up access for say VPN servers, email servers, and web servers but if you do this they should be tightly controlled by the firewall rules but this poses a bit of an issue for us. Let’s say we request a web page, the firewall checks our rules and allows the traffic through at some point that the webserver is going to respond right but if the firewall doesn’t allow inbound traffic what does it do?
Stateful Firewalls
Well, most firewalls are something called stateful firewalls. Stateful firewalls monitor active connections. This means that once outbound traffic has been allowed, the returning traffic is then accepted. This is great because we don’t need to add separate outgoing rules and separate incoming rules. Okay, so everything we’ve just discussed so far is known as a traditional firewall. It mostly uses firewall rules to block or allow traffic based on several things like IP address, port number, etc.
Next-Generation Firewalls
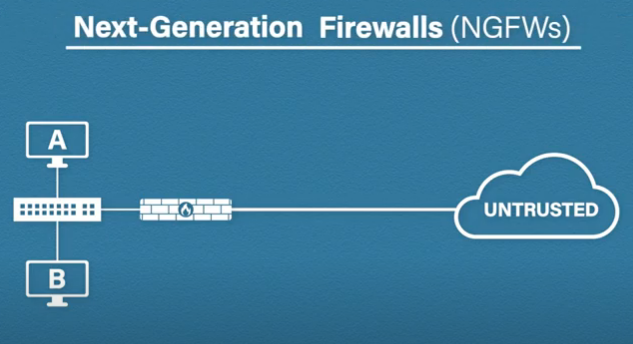
Now, next-generation firewalls take the same methods, but then they enhance them with more in-depth security features Quick warning, there are a lot of buzzwords out there and next-gen firewall is one of them. Different vendors will have slightly different meanings and features to what a next-gen firewall is or what theirs does but generally speaking this is what a next-generation firewall should include.
Application Level Inspection
In application-level infection, the firewall will try to identify the risky applications and also block them if they are not trusted. Intrusion prevention systems or IPS will inspect the contents of the traffic and look for patterns or signatures. It’s looking for malicious or malware-related traffic. IPS can also detect anomalies and unusual traffic external threat intelligence.
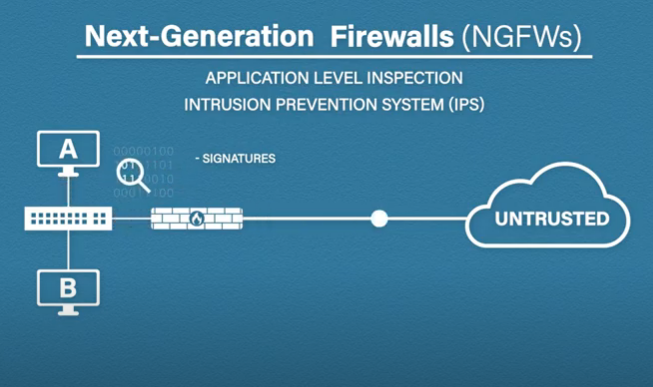
Next-generation firewalls can easily upgrade themselves from external threat intelligence sources. So, if a brand-new attack has been identified, the vendor can update the firewall’s threat intelligence to be able to identify this new emerging threat.
Features of Firewalls
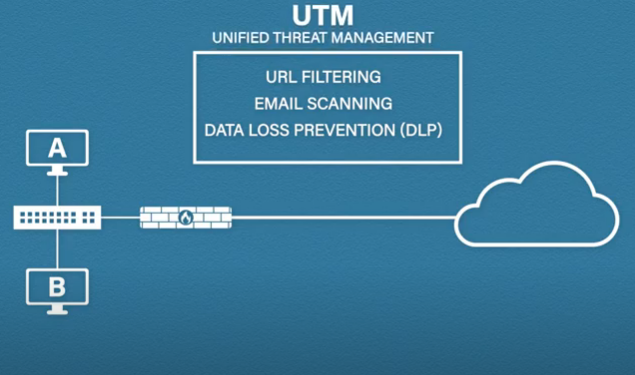
There are a huge number of features that firewalls can offer. Things like URL filtering, email scanning, data loss prevention, or DLP, and the list goes on and on firewalls that have features like these are often known as UTM s or unified threat management. The idea is you have a single appliance that unifies all of these security features.
So that is how a network firewall works, but you may have seen another type. Computers can also have software-based firewalls.
Windows Firewalls
The Windows Firewall is built-in and it uses the same rule-based methods such as port, destination, and source IP address. So you might be thinking why have a network and endpoint firewall? I prefer to consider it as a house. If you lock all of your internal doors would you be happy to leave the front door wide open and let the bad guys or wander your halls?
Probably not. If something gets past the network firewall the endpoint firewall is there to catch it. Also, what if the attack comes internally? The network firewall doesn’t see the traffic but the endpoint firewall does.
Conclusion
Now you have a basic understanding of Firewalls. If you want to more secure your network then you can use other solutions like a checkpoint. Firewalls are the advanced way to protect traffic and network and it’s also easy to use.


