Cybercriminals and other cyber attackers are known for riding on a brand’s popularity to trick users into thinking they’re dealing with legitimate companies’ representatives when they’re actually not. But organizations concerned with brand protection can ward off threats with the help of intelligence sources like WHOIS Database Download, more information on which is available at https://www.whoisxmlapi.com/whois-database-download.php.
Yet how can they go about it? Let’s take at several ways to identify possible instances of brand infringement.
The Perils That Non-Publicly Attributable Domains Pose
Contents
Starting off with an example, top 2 Fortune 500 company Amazon is no stranger to being the subject of tons of phishing emails such as:

Could the same be said of other large organizations?
This post features three recent studies that looked into the top 25 Fortune 500 companies’ potential attack surfaces, which could tarnish their reputation if not addressed, using a WHOIS database. We identified their exploitable attack surfaces by looking at existing domains that do not necessarily fall under their jurisdiction. Our first step? To identify the organizations and their respective official domains.
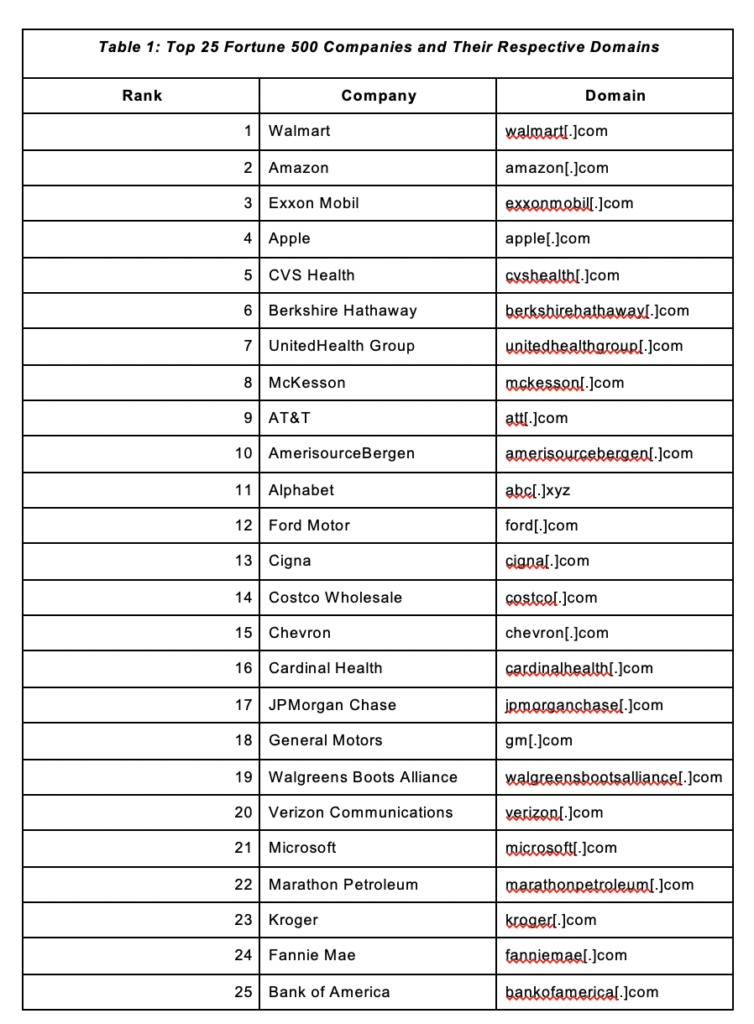
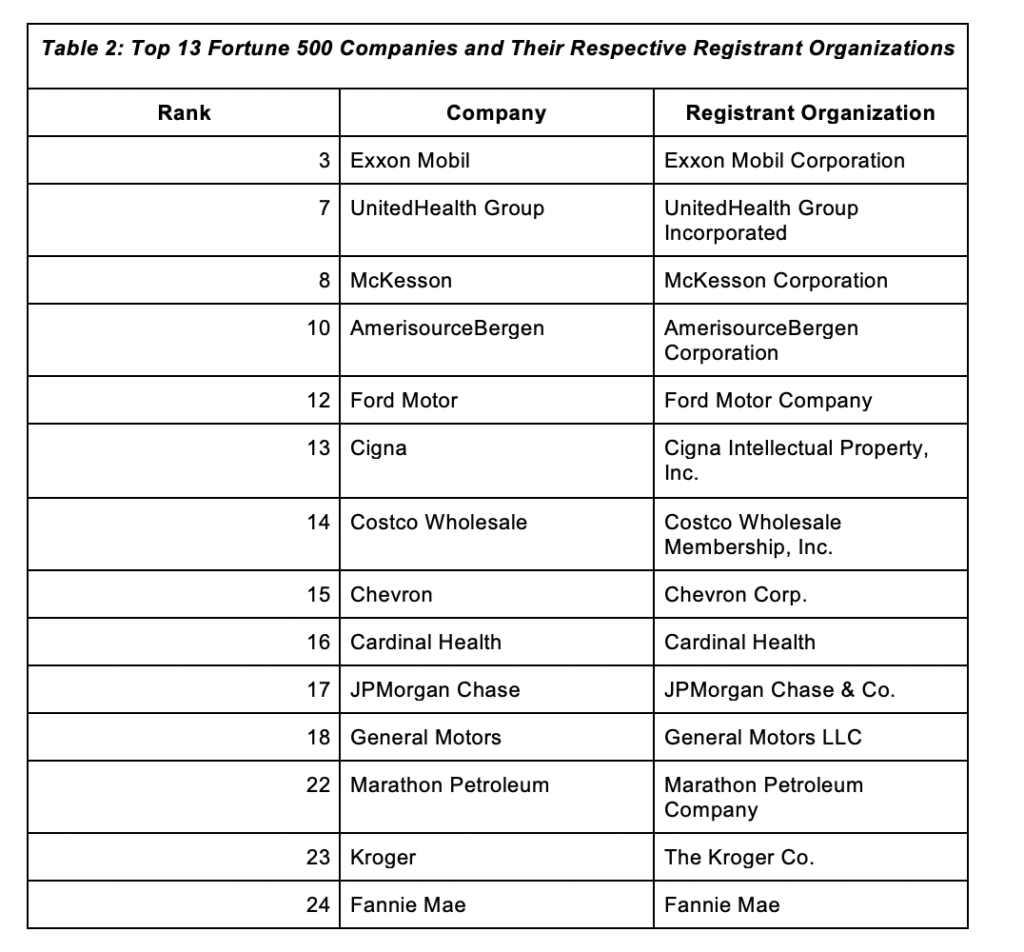
Case 1: Using the Registrant Organization as the Company Identifier
The first study began with a bulk WHOIS database lookup. The search results gave us a list of the companies’ corresponding registrant organization names shown below. Note that those who did not indicate their organization names and owned more of the domains than not were taken out of the sample.
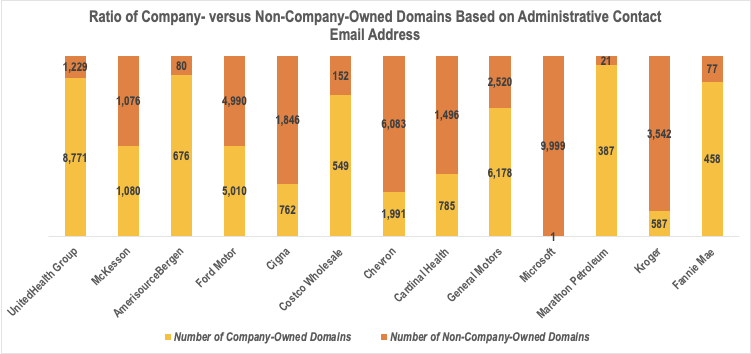
Using the information we obtained from the bulk WHOIS database lookup, we established that most of the domains containing the top 25 Fortune 500 companies’ brands were not under their control (see the figure below for a detailed comparison for each organization). In particular, only 68% or 43,211 out of the 63,215 domains are publicly attributable to the organizations in the reduced sample. These can figure in various malicious campaigns targeting their customers and tarnishing their reputation.
Case 2: Using the Administrative Contact Email Address as the Company Identifier
The second study used the administrative contact email address as a reverse WHOIS search term. We obtained the following data:
Despite the difference in company identifier, we yielded the same finding—many of the domains containing the Fortune 500 companies’ brands or names are not proven to be under their control. See the detailed comparison results in the figure below.
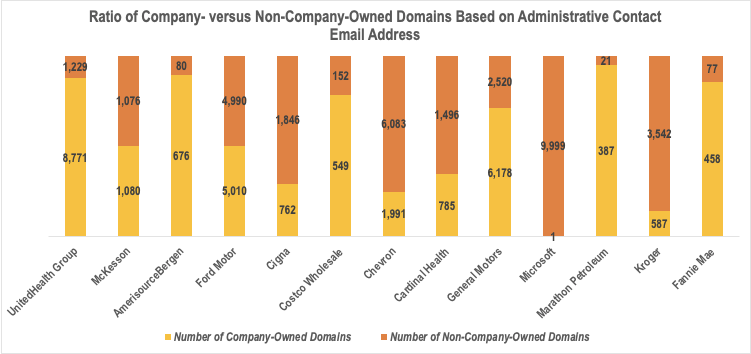
Following the same steps and using the same tools as the first study, the second investigation showed that 45% of the domains containing the Fortune 500 companies’ names could not be publicly attributed to them.
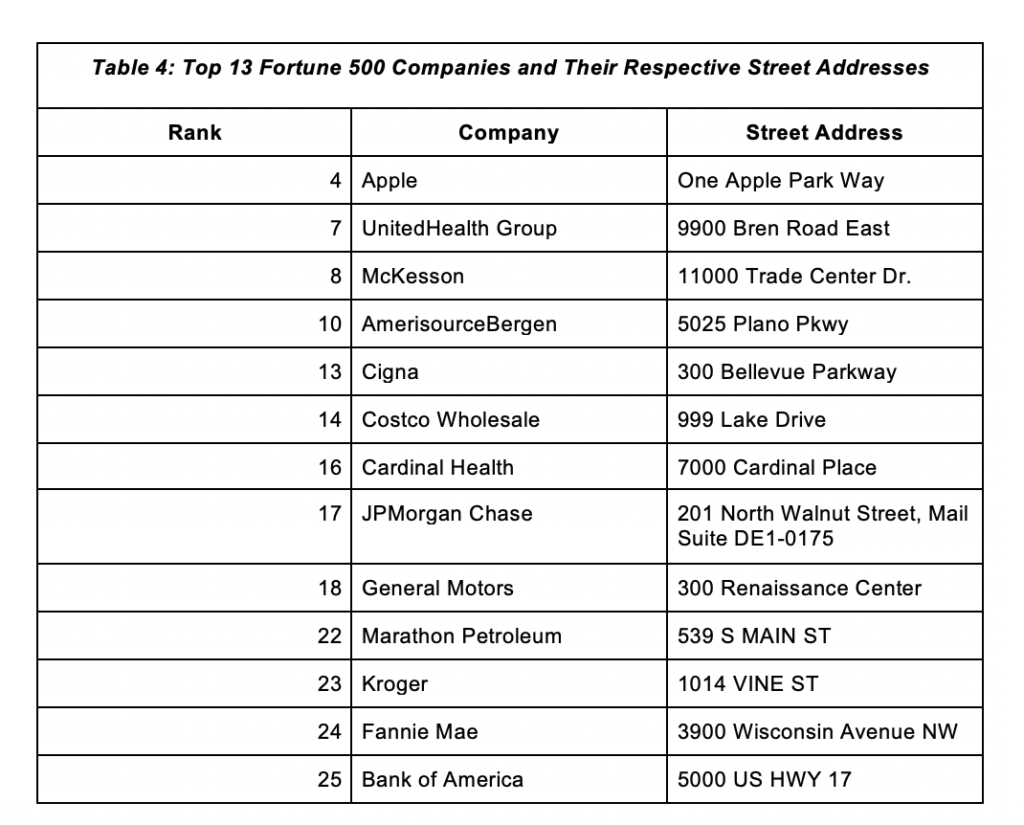
Case 3: Using the Company Street Address as the Company Identifier
Finally, the third study used the complete company street address for the reverse WHOIS searches. We ended up with a sample of 13 organizations shown in Table 4.
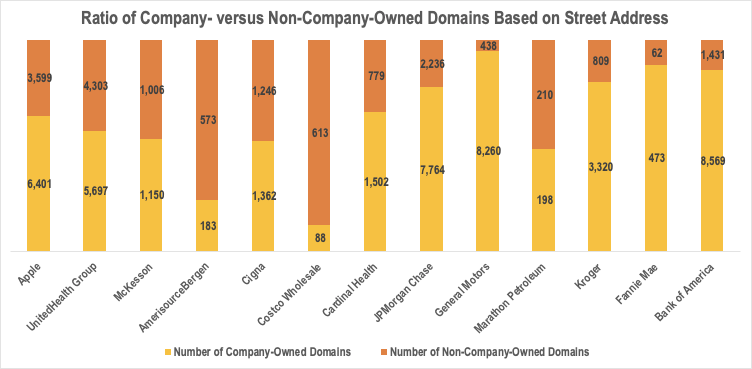
As usual, we took out the organizations that did not disclose their street addresses and owned more of the registered domain names than not from the sample. Out of the 44,967 domains that contain the brand names, 17,305 could be publicly attributed to the reduced sample. A detailed comparison of the publicly to non-publicly attributable domains is shown in the figure below.
The Verdict
As shown, regardless of the WHOIS database record detail used as a reverse WHOIS search term, one thing is clear—many of what we might think are domains associated with Fortune 500 companies; the truth is they are not. But without first determining identifiable company information from a WHOIS database, we would not have been able to subject all of the domains with the companies’ brands to further scrutiny.
—
Brand protection entails preventing cybersquatters and other counterfeiters from infringing an organization’s trademark rights. One way to start investigations to pinpointing who these threat actors are is by using tools like WHOIS Database Download. As the featured studies showed, determining a company’s digital footprints includes finding domains that use their brands but are not under their control. Once potential perpetrators have been identified, it would be easier for the mimicked brands to file dispute resolutions or request Internet service provider (ISP) takedown.


