About half of the world’s population turns to the Internet for business, information, and entertainment. And both small business owners and large enterprises can attest to the fact that the vast user base has resulted in radical changes in marketing, advertising, and other processes. Unfortunately, it has also attracted threat actors. Being able to tap just a percentage of the Internet-using population would mean more sensitive data to steal and more financial opportunities for cybercriminals.
One of threat actors’ tools, for instance, are newly registered domains. In a recent study where we subjected a list of indicators of compromise (IoCs) containing 2,300 domains, we found out that over 90% were newly registered.
It is, therefore, advisable for SOCs, MSSPs, and security platform providers to also glean domain intelligence from a newly registered domain (NRD) database[1] . That way, the threats that newly registered domains pose are lessened. That brings us to the following question: What risks can newly registered domains bring to a network? We explored this using Threat Intelligence Platform[2] .
3 Threats Newly Registered Domains Pose That Threat Intelligence Platform Can Catch
1. Phishing and Typosquatting
Aside from pretending to be someone else, such as in business email compromise (BEC) scams, phishing actors also use misspelled variations of reputable organizations’ domain names. The tactic is called “typosquatting,” and the domains, although misspelled, make emails look legitimate. Typosquatting also targets people who tend to mistype domain names.
Let’s examine one of the most impersonated brands among phishers, PayPal. On the newly registered database we downloaded dated 29 April 2020, we saw nine domains that use variations of the word “PayPal.”
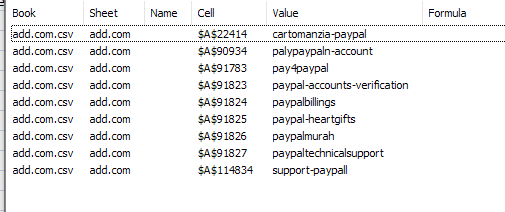
Five of them failed the Threat Intelligence Platform malware check and also had other configuration issues, namely:
- palypaypaln-account[.]com
- paypal-accounts-verification[.]com
- paypalbillings[.]com
- paypaltechnicalsupport[.]com
- support-paypall[.]com
2. Malware Infection
Most malware still get into networks via phishing emails. But like phishing, malware infections can also be avoided when users regularly monitor newly registered domains. Security teams can integrate an NRD database into their solutions as a domain intelligence source. By doing so, organizations proactively protect their networks instead of waiting for their systems to detect a malicious domain.
The Threat Intelligence Platform also allows security teams to dig deeper into newly registered domains. Zooming into the malicious domain paypal-accounts-verification[.]com, for example, the platform also revealed several other domains on the same IP address.
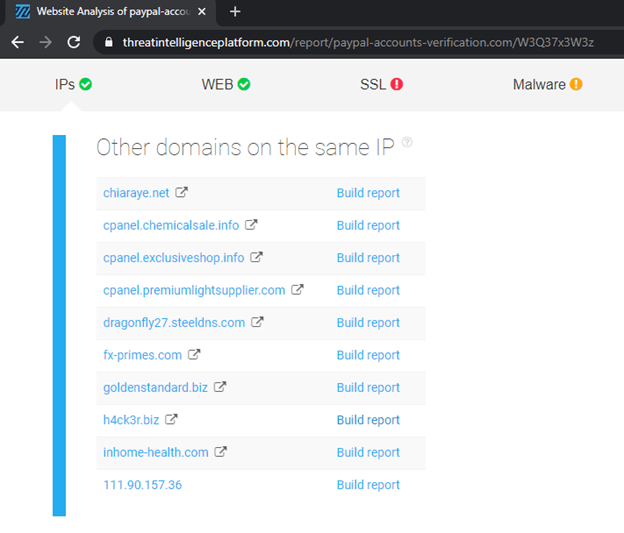
While being on that list is not conclusive evidence of maliciousness, all of the connected domains are also worth looking into. In the present case, there is a good chance that the registrant of paypal-accounts-verification[.]com is abusing a shared IP address connected to the domains above-cited. All these domain names could thus soon be penalized should the IP address end up blocked or listed on malware and phishing databases. The takeaway from this is that all website owners making use of shared IP addresses should regularly check if they are not sharing it with a malicious NRD.
3. Spamming
Like phishers and malware operators, spammers also continue to be a nuisance for organizations. And although there are tons of anti-spamming technologies out there, it would be wise to add NRD monitoring to their capabilities. To illustrate, below are two examples of spam emails.
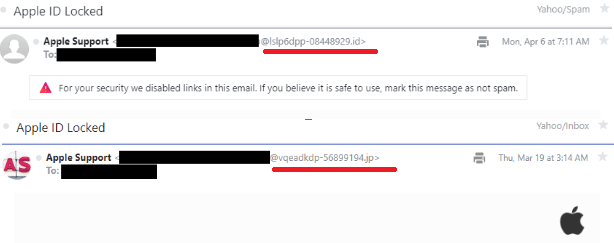
If you notice, the email domains look like random combinations of alphanumeric characters that are likely generated by a domain generation algorithm. Since these providers regularly need fresh domains, they could be doing bulk registrations of random and nonsensical domain names.
There are several domains on the NRD database that look very similar to the spamming email domain. Some of them are:
- 00c64c0c932183964cdc5a0e13b1b38d[.]com
- 09yym2tv1dmst[.]com
- 0vmb5bmdizce2gu[.]com
- 0wwki0cbbfmst[.]com
Each of the domains above is suspected of ties to malicious activities.
To put it bluntly, a lot of, if not all newly registered domains need to be monitored. Integrating an NRD database into security processes, solutions, and systems can help protect networks better from the threats that recently registered domains bring.


