The recent influx of technologies at various digital platforms has empowered industries to connect with their customers through smart mobile applications and desktop devices. We see the world transforming into a huge digital bubble. But a threatening proliferation of malware and malicious software is also getting ready to pry into your systems.
As a preventive measure, any business would need a sturdy and highly responsive security system that can protect their devices and applications from such threats and data losses. Software publishers and mobile network providers now increasingly require code signing from trusted certificate authorities before accepting code for distribution.
This is because signing code enables applications and software developers to develop trust in their users and helps the users to ensure that their applications have not been tampered with by any third-party and are backed up and created by a legitimate entity.
EV Code Signing Certificates is empowered to go beyond the expectations of the users in terms of providing security with an exquisite protective layer to the software developers.
What is EV Code Signing Certificate?
Contents [show]
An EV code signing certificate is a file comprising of a digital signature that is exclusively used for signing executables and scripts. Further, the sign codes help to verify the developer’s identity and guarantee non-tampering of the code as it is signed.
In this manner, users can verify the trustworthiness of the software. Unlike a normal code signing certificate, an EV code signing certificate requires the developer to undergo a further validation process.
Highly trusted by Microsoft Smartscreen Filter, the EV Code signing certificate serves to be ideal for signing device drivers and other high-trust software.
Key Features & Benefits of EV Code Signing Certificate
Extended Validation Code Signing Certificate encompasses all-inclusive benefits of normal code signing and also represents some critical security features that amplify security and augment customer trust.
Two-Factor Authentication
Before you buy the certificate, an encrypted token is sent and includes the private keys stored on a USB device. While signing code with your Comodo EV Code Signing Certificate, the physical devices are used to make sure that no unauthorized developer or user is exporting or using your certificate.
Time-Sensitive Signing
EV Signing Code Certificate empowers you to insert a token and use private keys to digitally sign and timestamp your software. By process, the moment EV validation code signing certificate gets added a timestamp, your signature lives even if the original certificate gets expired.
Instant SmartScreen Reputation
Gaining an immediate reputation from Microsoft SmartScreen, Microsoft recognizes you as a reputed, dignified, and upstanding business after the extended validation. Decreasing warning messages to the users increases brand reputation and builds enough trust in users to help you gain better conversions.
Hardware Security Module (HSM) Support
To obtain better control over your certificate and the private keys, you can install an EV code signing certificate on HSMs. The authorized staff of your company can access the HSM and use the certificate to sign codes.
Universal Platform Compatibility
As and when you make changes to the file, the certificate gets automatically updated for different platforms such as Authenticode and Kernel Mode.
Effective & Affordable
With an instant trust given to the end-users, EV code signing certificate proves to be affordable and cost-effective for your business.
How does EV Code Signing Certificate Work?
During the issue of Sectigo EV Code Signing Certificate, the private key is mailed physically on an external hardware token to ensure protection against unauthorized access. This is done to prevent anyone from illegal access to your network. A digital security issue is turned into a physical security issue.
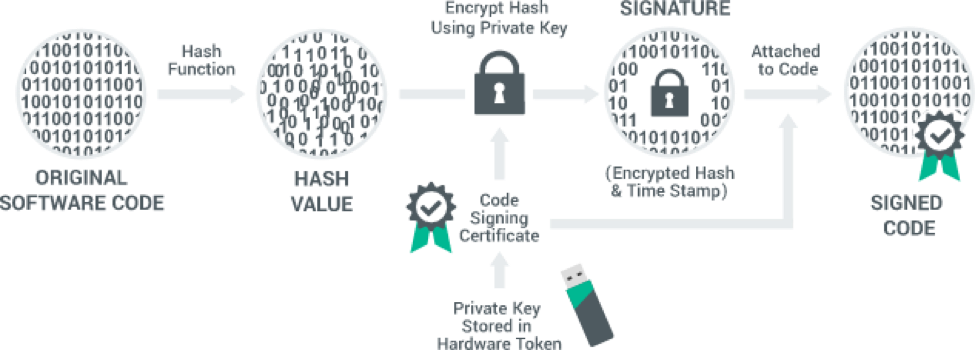
Hashing
Once the software is created, it is hashed. Hashing enables users to identify if the software is tampered with. When download produces an incorrect hash value, the browsers can find out the compromises.
Signing
Further, the external hardware token is inserted and the private key is used to digitally sign and timestamp your software. In this manner, browsers identify the publishers’ identity and help to decide whether to trust or not.
Download
After the software gets hashed, signed, and timestamped, you can further post for download.
As and when a customer tries to download, the browser will identify the publisher details, decides upon the trust factor, and checks if it is tampered with.
Final Thoughts
Way forward, we are heading towards a revolutionary phase of the digital era. EV Code signing certificates soon are going to become inevitably compulsory for security and safety. When everyone has begun using it, join the revolutionary rally of this transformation. Strengthen your security and your reputation!


